A discussion how backup storage needs to be made safe and secure, too, especially if companies need to quickly right themselves after an attack.
Dana Gardner: Hi, this
is Dana Gardner,
Principal Analyst at Interarbor
Solutions, and you are listening to BriefingsDirect. New threats to data
security are emerging
all the time. Bad players constantly seek new ways to get at and exploit
sensitive data sources.
 |
| Gardner |
This next BriefingsDirect data
security insights discussion explores how data, from one end of its life cycle
to the other, needs new protection and a means for rapid recovery.
Stay with us as we examine how
backup storage especially needs to be made safe and secure if companies want to
quickly right themselves from an attack. To learn more, please welcome Andrew Peters,
Stealth Industry Director at Unisys. Welcome,
Andrew.
Andrew Peters: Thank
you.
Gardner: We’re
also here with George Pradel,
Senior Systems Engineer at Dell
EMC. Welcome, George.
George Pradel: Hi, Dana. Thanks for having us.
Gardner: Andrew,
what’s changed in how data is being targeted? How are things different from three
years ago?
 |
| Peters |
Peters: Well,
one major thing that’s changed in the recent past has been the fact that the bad
guys have found out how to monetize
and extort money from organizations to meet their own ends. This has been
something that has caught a lot of companies flatfooted -- the sophistication
of the attacks and the ability to extort money out of organizations.
Gardner:
George, why does all data -- from one end of its life cycle to the other --now
need to be reexamined for protection?
Pradel: Well,
Andrew brings up some really good points. One of the things we have seen out in
the industry is ransomware-as-a-service.
Folks can just dial that in. There are service level agreements (SLAs) on it. So
everyone’s data now is at risk.
Another of the things that we
have seen with some of these attacks is that these people are getting a lot
smarter. As soon as they go in to try and attack a customer, where do they go
first? They go
for the backups. They want to get rid of those, because that’s kind of like
the 3D chess where you are playing one step ahead. So things have changed quite
a bit, Dana.
Peters: Yes,
it’s really difficult to put the squeeze on an organization knowing that they
can recover themselves with their backup data. So, the heat is on the bad guys
to go after the backup systems and pollute that with their malware, just to
keep companies from having the capability to recover themselves.
Gardner: And
that wasn’t the case a few years ago?
 |
| Pradel |
Pradel: The
attacks were so much different a few years ago. They were what we call script kiddie attacks,
where you basically get some malware or maybe you do a denial-of-service
attack. But now these are programmatized, and the big thing about that is
if you are a target once, chances are really good that the thieves are just
going to keep coming back to you, because it’s easy money, as Andrew pointed
out.
Gardner: How has
the data storage topology changed? Are organizations backing up differently
than they did a few years ago as well? We have more cloud use, we have hybrid, and
different strategies for managing de-dupe and other redundancies. How has the
storage topology and landscape changed in a way that affects this equation of
being secure end to end?
The evolution of backup plans
Pradel: Looking
at how things have changed over the years, we started out with legacy systems,
the physical systems that many of us grew up with. Then virtualization came
into play, and so we had to change our backups. And virtualization offered up
some great ways to do image-level backups and such.
Now, the big deal is cloud. Whether
it’s one of the public cloud vendors, or a private cloud, how do we protect
that data? Where is our data residing? Privacy and security are now part of the
discussion when creating a hybrid cloud. This creates a lot of extra confusion --
and confusion is what thieves zone in on.
We want to make sure that no
matter where that data resides that we are making sure it’s protected. We want
to provide
a pathway for bringing back the data that is air gapped or via
one of our other technologies that helps keeps the data in a place that allows
for recoverability. Recoverability is the number one thing here, but it
definitely has changed in these last few years.
Gardner:
Andrew, what do you recommend to customers who may have thought that they had
this problem solved? They had their storage, their backups, they protected
themselves from the previous generations of security risk. When do you need to
reevaluate whether you are secure enough?
Stay prepared
Peters: There
are a few things to take into consideration. One, they should have an operation
that can recover their data and bring their business back up and running. You
could get hit with an attack that turns into a smoking hole in the middle of
your data center. So how do you bring your organization back from that without
having policies, guidance, a process and actual people in place in the systems
to get back to work?
Another thing to consider is
the efficacy of the data. Is it clean? If you are backing up data that is
already polluted with malware, guess what happens when you bring it back out and
you recover your systems? It rehydrates itself within your systems and you still
have the same problem you had before. That’s where the bad guys are paying
attention. That’s what they want to have happen in an organization. It’s a hand
they can play.
If the malware can still come
out of the backup systems and rehydrate itself and re-pollute the systems when an
organization is going through its recovery, it’s not only going to hamper the
business and the time to recovery, and cost them, it’s also going to force them
to pay the ransoms that the bad guys are extorting.
Gardner: And
to be clear, this is the case across both the public and the private sector. We
are hearing about ransomware
attacks in lots of cities and towns. This is an equal opportunity risk, isn’t
it?
Peters:
Malware and bad guys don’t discriminate.
Pradel: You are
exactly right about that. One of the customers that I have worked with recently
in a large city got hit with a ransomware attack. Now, one of the things about
ransomware attacks is that they typically want you to pay in bitcoin. Well, who
has $100,000 worth of bitcoin sitting around?
If you have a government attacked, one of the problems is that chaos ensues. Police officers in their cars were not able to pull up license plates on the computer to check on cars they were pulling over.
But let’s take a look at why it’s so important to eliminate these types of attacks. If you have a government attacked, one of the problems is that chaos ensues. In one particular situation, police officers in their cars were not able to pull up license plates on the computer to check on cars they were pulling over, to see if they had a couple of bad tickets or perhaps the person was wanted for some reason. And so it is a very dangerous situation you may put into play for all of these officers.
That’s one tiny example of how
these things can proliferate. And like you said, whether it’s public sector or private
sector, if you are a soft target, chances are at some point you are going to
get hit with ransomware.
Secure the perimeter and beyond
Gardner: What
are we doing differently in terms of the solutions to head this off, especially
to get people back and up and running and to make sure that they have clean and
useable data when they do so?
Peters: A lot
of security had been predicated on the concept of a perimeter, something where
we can put up guards, gates, and guns and in a moat. There is an inside and an
outside, and it’s generally recognized today that that doesn’t really exist.
And so, one of the new moves
in security is to defend the endpoint, the application, and to do that using a
technology called micro-segmentation. It’s becoming more popular because it allows
us to have a security perimeter and a policy around each endpoint. And if it’s done
correctly, you can scale to hundreds to thousands to hundreds of thousands, and
potentially millions of endpoint devices, applications, servers and virtually
anything you have in an environment.
And so that’s one big change:
Let’s secure the endpoint, the application, the storage, and each one comes with
its own distinct security policy.
Gardner:
George, how do you see the solutions changing, perhaps more toward the holistic
infrastructure side and not just the endpoint issues?
Pradel: One
of the tenets that Andrew related to is called security by
obscurity. The basic tenet is, if you can’t see it’s much safer. Think
about a safe in your house. If the safe is back behind the bookcase and you are
the only person that knows it’s there, that’s an extra level of security. Well,
we can do that with technology.
So you are seeing a lot of
technologies being employed. Many of them are not new types of security
technologies. We are going back to what’s worked in the past and building some
of these new technologies on that. For example, we add on automation, and with
that automation we can do a lot of these things without as much user
intervention, and so that’s a big part of this.
Incidentally, if any type of
security that you are using has too much user intervention, then it’s very hard
for the company to cost-justify those types of resources.
Gardner: Something
that isn’t different from the past is having that Swiss Army knife approach of
multiple layers of security. You use different tools, looking at this as a team
sport where you want to bring as many solutions as possible to bear on the
problem.
How have Unisys and
Dell EMC brought different strengths together to create a whole greater
than the sum of the parts?
Hide the data, so hackers can’t seek
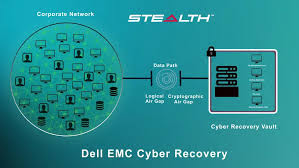
Peters: One
thing that’s fantastic that Dell has done is that they have put together a Cyber
Recovery solution so when there is a meltdown you have gold copies of
critical data required to reestablish the business and bring it back up and get
into operation. They developed this to be automated, to contain immutable
copies of data, and to assure the efficacy of the data in there.
Now, they have set this stuff up
with air gapping, so it is virtually isolated from any other network
operations. The bad guys hovering around in the network have a terrible time of
trying to even touch this thing.
Unisys put what we call a
cryptographic wrapper around that using our micro-segmentation technology
called Stealth.
This creates a cryptographic air gap that virtually disappears that vault and
its recovery operations from anything else in the network, if they don’t have a
cryptographic key. If they have a cryptographic key that was authorized, they
could talk to it. If they don’t, they can’t. So any bad guys and malware can’t see
it. If they can’t see, they can’t touch, and they can’t hack. This then turns
into an extraordinarily secure means to recover an organization’s operations.
Gardner: The
economics of this is critical. How does your technology combination take the
economic incentive away from these nefarious players?
Pradel: Number
one, you have a way to be able to recover from this. All of a sudden the bad
guys are saying, “Oh, shoot, we are not going to get any money out of these
guys.”
You are not going to be a constant target. They are going to go after your backups. Unisys Stealth can hide the targets that these people go after. Once you have this type of a Cyber Recovery solution in place, you can rest a lot easier at night.
As part of the Cyber
Recovery solution, we actually expect malware to get into the Cyber
Recovery vault. And people shake their head and they go, “Wait, George, what do
you mean by that?”
Yes, we want to get malware
into the Cyber Recovery vault. Then we have ways to do analytics to see whether
our point-in times are good. That way, when we are doing that restore, as
Andrew talked about earlier, we are restoring a nice, clean environment back to
the production environment.
Recovery requires commitment, investment
So, these
types of solutions are an extra expense, but you have to weigh the risks for
your organization and factor what it really costs if you have a cyber recovery incident.
Additionally, some people may
not be totally versed on the difference between a disaster recovery
situation and a cyber recovery situation. A disaster recovery may be from some
sort of a physical problem, maybe a tornado hits and wipes out a facility or
whatever. With cyber recovery, we are talking about files that have been
encrypted. The only way to get that data back -- and get back up and running --
is by employing some sort of a cyber recovery solution, such as the
Unisys and Dell EMC solution.
Gardner: Is this
tag team solution between Unisys and Dell EMC appropriate and applicable to all
kinds of business, including cloud providers or managed service providers?
Peters: It’s really
difficult to measure the return on investment (ROI) in security, and it always
has been. We have a tool that we can use to measure risk, probability, and
financial exposure for an organization. You can actually use the same
methodologies that insurance companies use to underwrite for things like
cybersecurity and virtually anything else. It’s based on the reality that there
is a strong likelihood that there is going to be a security breach. There is
going to be perhaps a disastrous security breach, and it’s going to really hurt
the organization.
Plan on the fact that it's probably going to happen. You need to invest in your systems and your recovery. If you think you can sustain a complete meltdown on your company and go out of operations for weeks to months, then you probably don't need to put money into it.
Plan on the fact that it’s probably going to happen. You need to invest in your systems and your recovery. If you think that you can sustain a complete meltdown on your company and go out of operation for weeks to months, then you probably don’t need to put money into it.
If you understand how exposed
that you potentially are, and the fact that the bad guys are staring at the low
hanging fruit -- which may be state governments, or cities, or other things
that are less protected.
The fact is, the bad guys are
extraordinarily patient. If your payoff is in the tens of millions of dollars,
you might spend, as the bad guys did with Sony, years
mapping systems, learning how an operation works, and understanding their
complete operations before you actually take action, and in potentially the
most disastrous way possible.
So ergo, it’s hard to put a
number on that. An organization will have to decide how much they have to lose,
how much they have at risk, and what the probability is that they are actually
going to get hit with an attack.
Gardner:
George, also important on this applicability as to where it’s the right fit is
that automation and skills. What sort of organizations typically will go at
this and what skills are required?
Automate and simplify
Pradel: That’s
been the basis for our Cyber Recovery solution. We have written a number of
APIs to be able to automate different pieces of a recovery situation. If you
have a cyber recovery incident, it’s not a matter of just, “Okay, I have the
data, now I can restore it.” We have a lot of experts in the field. What they
do is figure out exactly where the attack came from, how it came in, what was
affected, and those types of things.
We make it as simple as
possible for the administration. We have done a lot of work creating APIs that
automate items such as recovering backup servers. We take point-in-time copies
of the data. I don’t want to go into it too deeply, but our data domain
technology is the basis for this. And the reason why it’s important to note is
because the replication we do is based upon our variable-length
deduplication.
Now, that may sound a little
gobbledygook, but what that means is that we have the smallest replication
times that you could have for a certain amount of data. So when we are taking
data into the Cyber Recovery vault, we are reducing what’s called our dwell time. This is the
area where you would have someone that could see that you had a connection
open.
But a big part of this is on a
day-to-day basis, I don’t have to be concerned. I don’t have a whole team of
people that are maintaining this Cyber Recovery vault. Typically, with our
customers, they already have the understanding of how our base technology works
and so that part is very straightforward. And what we have is automation, we
have policies that are set up in the Cyber Recovery vault that will, on a
regular basis, hold the data, whatever is changed from the production
environment, typically once a day.
And a rule of thumb for some
people that might be thinking, this sounds really interesting, but how much
data would I put in this? Typically we’ll do 10 to 15 percent of a customer’s
production environment, that might go into the Cyber Recovery vault. So we want
to make this as simple as possible, we want to automate as much as possible.
And on the other side, when
there is an incident, we want to be able to also automate that part because
that is when all heck is going on. If you’ve ever been involved in one of those
situations, it’s not always your clearest thinking moment. So automation is your
best friend and can help you get back up and running as quickly as possible.
Gardner:
George, run us through an example, if you would, of how this works in the
real-world.
One step at a time for complete recovery
Pradel: What
will happen is that at some point somebody clicks on that doggone attachment
that was on that e-mail that had a free trip to Hawaii or something and it had
a link to some ransomware.
Once the security folks have
determined that there has been an attack, sometimes it’s very obvious. There is
one attack where there is a giant security skeleton that comes up on your
screen and basically says, “Got you.” It then gives instructions on how you
would go about sending them the money so that you can get your data back.
However,
sometimes it’s not quite so obvious. Let’s say your security folks have
determined there has been attack and then the first thing that you would want
to do is access the cyber recovery provided by putting the Cyber Recovery vault
with Stealth. You would go to the Cyber Recovery vault and lock down the vault,
and it’s simple and straightforward. We talked about this a little earlier
about the way we do the automation is you click on the lock, that locks
everything down and it stops any future replications from coming in.
And while the security team is
looking to find out how bad it is, what was affected, one of the things the
cyber recovery team does is to go in and run some analysis, if you haven’t done
so already. You can automate this type of analysis, but let’s say you haven’t
done that. Let’s say you have 30 point-in times, so one for each day throughout
the last month. You might want to check and run an analysis against maybe the
last five of those to be able to see whether or not those come up as suspicious
or as okay.
The way that’s done is to look
at the entropy of the different point-in-time backups. One thing to note is
that you do not have to rehydrate the backup in order to analyze it. So let’s
say you backed it up with Avamar
and then you wanted to analyze that backup. You don’t have to rehydrate that in
the vault in order to get it back up and running.
Once that’s done, then there’s
a lot of different ways that you can decide what to do. If you have physical
machines but they are not in great shape, they are suspect in that. But, if the
physical parts of it are okay, you could then decide that at some point you’re
going to reload those machines with the gold copies or very typical to have in
the vault and then put the data and such on it.
If you have image-level
backups that are in the vault, those are very easy to get back up and running
on a VMWare ESX
host store, or Microsoft
Hyper-V host that you have in your production environment. So, there are a
lot of different ways that you can do that.
The whole idea, though, is
that our typical Cyber Recovery solution is air-gapped and we recommend
customers have a whole separate set of physical controls as well as the
software controls.
Now, one of those steps may
not be practical in all situations. That’s why we looked at Unisys Stealth, to
provide a virtual air gap by installing the pieces from Stealth.
Remove human error
Peters: One
of the things I learned in working with the United
States Air Force’s Information Warfare Center was the fact that you can
build the most incredibly secure operation in the world and humans will do
things to change it.
With Stealth, we allow
organizations to be able to get access into the vault from a management
perspective to do analytics, and also from a recovery perspective, because
anytime there’s a change to the way that vault operates, that’s an opportunity
for bad guys to find a way in. Because, once again, they’re targeting these
systems. They know they’re there; they could be watching them and they can be
spending years doing this and watching the operations.
Unisys Stealth removes the
opportunity for human error. We remove the visibility that any bad guys, or any
malware, would have inside a network to observe a vault. They may see data flowing
but they don’t know what it’s going to, they don’t know what it’s for, they can’t
read it because it’s going to be encrypted. They are not going to be able to
even see the endpoints because they will never be able to get an address on
them. We are cryptographically disappearing or hiding or cloaking, whatever
word you’d like to use -- we are actively removing those from visibility from
anything else on the network unless it’s specifically authorized.
Gardner: Let’s
look to the future. As we pointed out earlier in our discussion, there is a
sort of a spy versus spy, dog chasing the cat, whatever you want to use as a
metaphor, one side of the battle is adjusting constantly and the other is
reacting to that. So, as we move to the future, are there any other machine learning
(ML)-enabled analytics on these attacks to help prevent them? How will we be
able to always stay one step ahead of the threat?
Peters: With
our technology we already embody ML. We can do responses called dynamic
isolation. A device could be misbehaving and we could change its policy and be
able to either restrict what it’s able to communicate with or cut it off
altogether until it’s been examined and determined to be safe for the
environment.
We can provide a lot of
automation, a lot of visibility, and machine-speed reaction in response to
threats as they are happening. Malware doesn’t have to get that 20-second head
start. We might be able to cut off in 10 seconds and be able to make it a
dynamic change to the threat surface.
Gardner: George,
what’s in the future that it’s going to allow you to stay always one step ahead
of the bad guys? Also, is there is an advantage for organizations doing a lot
of desktops-as-a-service (DaaS) or virtual desktops? Do they have an advantage
in having that datacenter image of all of the clients?
Think like a bad guy
Pradel: Oh, yes,
definitely. How do we stay in front of the bad guys? You have to think like the
bad guys. And so, one of the things that you want to do is reduce your attack
surface. That’s a big part of it, and that’s why the technology that we use to
analyze the backups, looking for malware, uses 100 different types of objects
of entropy.
As we’re doing ML of that data,
of what’s normal what’s not normal, we can figure out exactly where the issues
are to stay ahead of them.
Now an air gap on its own
surface is extremely secure because it keeps that data in an environment where
no one can get at it. We have situations where Unisys Stealth helped with closing
the air gap situation where a particular general might have three different
networks that they need to connect to and Stealth is a fantastic solution for
that.
If you’re doing DaaS, there
are ways that it can help. We’re always looking at where the data resides, and
most of the time in those situations the data is going to reside back at the
corporate infrastructure. That’s a very easy place to be able to protect data.
When the data is out on laptops and things like that, then it makes it a little
bit more difficult, not impossible, but you have a lot of different end points
that you’re pulling from. To be able to bring the system back up -- if you’re
using virtual desktops, that kind of thing, actually it’s pretty
straightforward to be able to do that because that environment, chances are
they’re not going to bring down the virtual desktop environment, they’re going
to encrypt the data.
Now, that said, one of the
things when we’re having these conversations, it’s not as straightforward of a
conversation as ever. We talk about how long you might be out of business
depending upon what you’ve implemented. We have to engineer for all the
different types of malware attacks. And what’s the common denominator? It’s the
data and keeping that data safe, keeping that data so it can’t be deleted.
We have a retention lock
capability so you can lock that up for as many as 70 years and it takes two
administrators to unlock it. That’s the kind of thing that makes it robust.
In the old days, we would do a
WORM drive and
copy stuff off to a CD to make something immutable. This is a great way to do
it. And that’s one way to stay ahead of the bad guys as best as we can.
Gardner: I’m
afraid we’ll have to leave it there. You have been listening to a sponsored
BriefingsDirect discussion on how data from one end of its lifecycle to the
other needs protection and a means for rapid recovery.
And we’ve learned how a
solution from Dell EMC and Unisys helps protect storage including backup data
and further assists companies in making themselves whole again after an attack --
when they’ve taken the proper precautions.
Please join me in thanking our
guests, Andrew Peters, Stealth Industry Director at Unisys. Thank you, Andrew.
Peters: Thank
you.
Gardner: And
George Pradel, Senior Systems Engineer at Dell EMC. Thank you so much, George.
Pradel: Thanks, Dana.
Gardner: And a
big thank you as well to our audience for joining this BriefingsDirect Data
Security Insights Discussion. I’m Dana Gardner, Principal Analyst at Interarbor
Solutions, your host throughout this series of Unisys-sponsored BriefingsDirect
discussions.
Thanks again for listening.
Please pass this along to your community and do come back next time.
A discussion how backup storage needs to be made safe and
secure, especially if companies need to right themselves from an attack. Copyright
Interarbor Solutions, LLC, 2005-2019. All rights reserved.
You may also be
interested in:
- How Unisys and Microsoft team up to ease complex cloud adoption for governments and enterprises
- Data-driven and intelligent healthcare processes improve patient outcomes while making the IT increasingly invisible
- Data-driven and intelligent healthcare processes improve patient outcomes while making the IT increasingly invisible
- How The Open Group Healthcare Forum and Health Enterprise Reference Architecture cures process and IT ills
- The next line of defense—How new security leverages virtualization to counter sophisticated threats
- Expert Panel Explores the New Reality for Cloud Security and Trusted Mobile Apps Delivery
- How IT innovators turn digital disruption into a business productivity force multiplier
- How the Citrix Technology Professionals Program produces user experience benefits from greater ecosystem collaboration





No comments:
Post a Comment